Day 11: Trashcan | Huntress CTF 2025 Write-Up
Huntress CTF 2025 - Day 11: Trashcan
Out of the challenges I have completed in the 2025 Huntress CTF, this was probably one of my favorites. The following is the description for this challenge:
Have you ever done forensics on the Recycle Bin? It’s… a bit of a mess. Looks like the threat actor pulled some tricks to hide data here though.
The metadata might not be what it should be. Can you find a flag?
Initial Analysis
After reviewing the text files, it was clear that files starting with $I contained metadata for deleted files while files starting with $R contain the contents of the deleted file. Visually, this data appears to have been recovered from the Recycling Bin on a Windows machine. However, there was something odd about it…
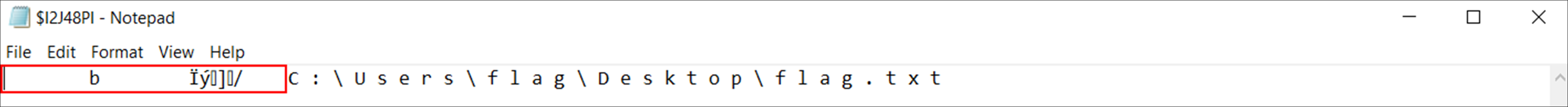
Each file had an abnormal piece of data in the metadata portion. For example, the below file contains the letter b.
Parsing Through the Data
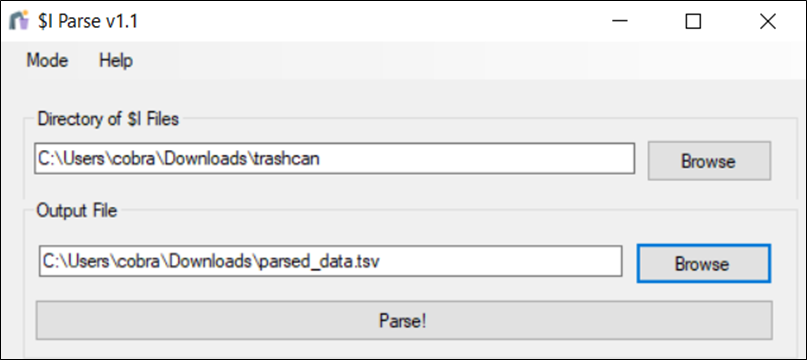
At first, I tried to decode each of these manually, but it was difficult to detect a pattern. Eventually, I stumbled upon the $I_Parse.exe tool which can parse the metadata from the $I metadata files. As shown below, you simply point the tool at the folder containing the $I files, specify an output file, and click on the Parse! button.
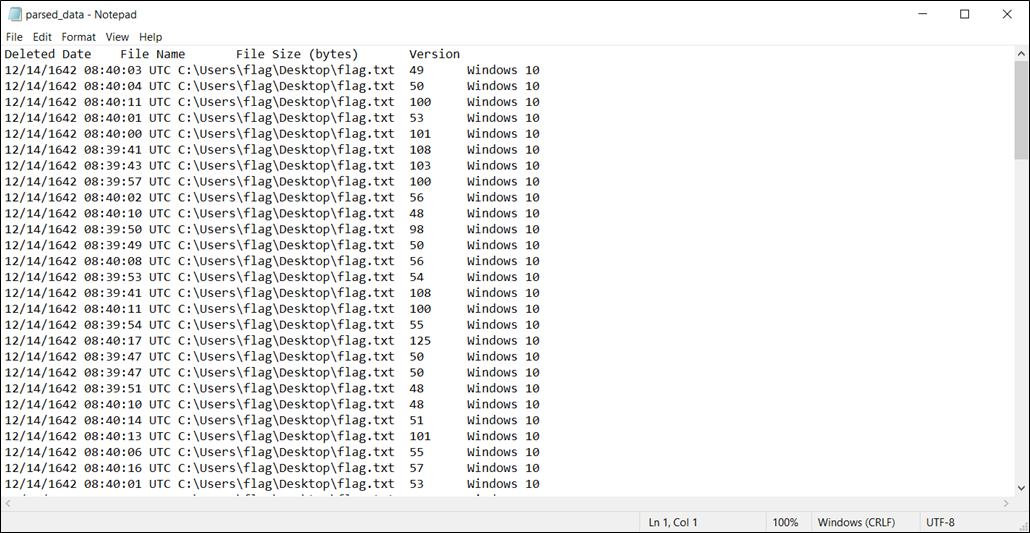
The $I_Parse.exe tool creates a file that looks like this:
Further Analysis
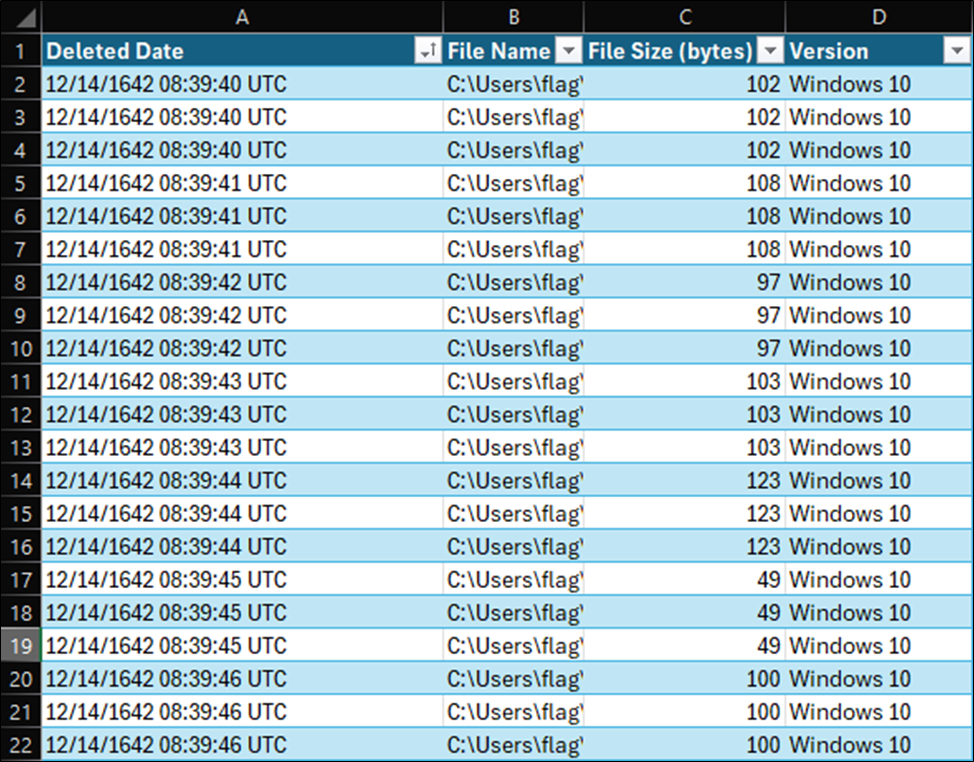
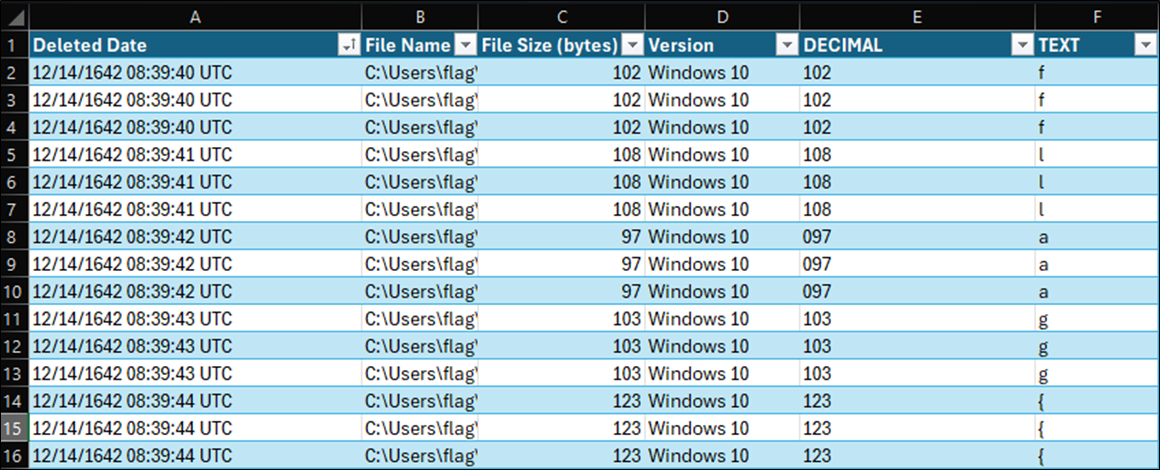
So I could more easily manipulate the data, I copied the above text file into Microsoft Excel. The most logical next step was to sort the lines by the date. In Excel, I created a table to easily do this. As you can see, when the file is sorted by date, the File Size (bytes) column is repeated exactly three times in a row for each number. For example, you can see a pattern of 102, 102, 102, 108, 108, 108, and so on . . .
Recognizing the Pattern
Now we have a recognizable and potentially useful pattern. Next, how do we convert those numbers to human readable text to obtain the flag? Well, the numbers are very consistent with decimal encoding. If we convert those decimal values to text, you can see it begins the text ffflllaaaggg{{{ though it seems each character is repeated three times.
Identifying the Flag
Using some Excel formulates, I combined all of the rows into a single line of text which returned the following string. However, you’ll notice it has three of each character.
ffflllaaaggg{{{111ddd222bbb222bbb000555666777111eeeddd111eeeeee555888111222666777888888555000ddd555eee333222999}}}
Using another formula in Excel, I removed the extra characters to reveal the final flag.
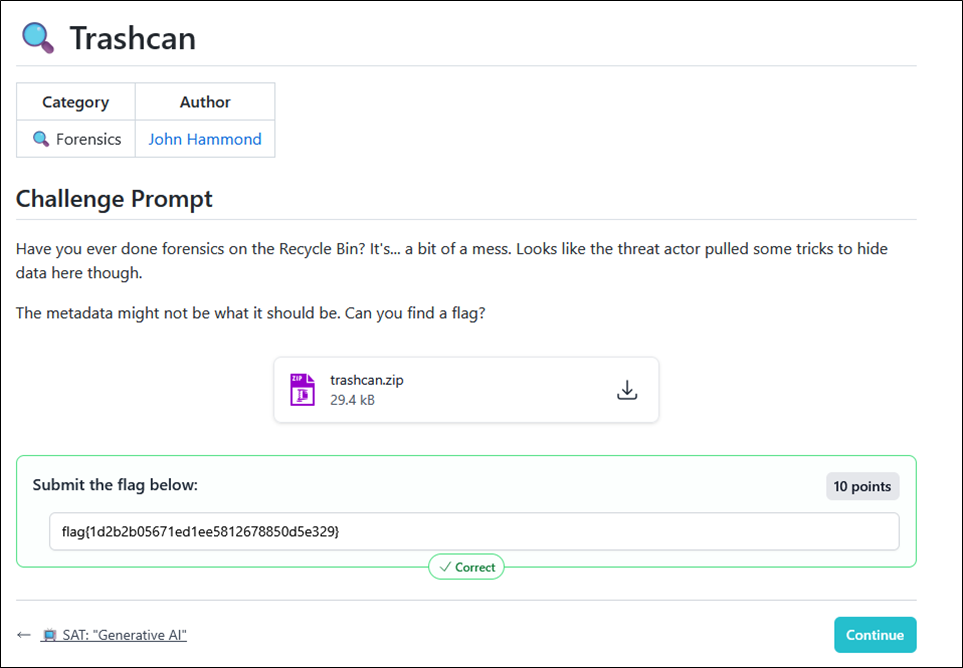
flag{1d2b2b05671ed1ee5812678850d5e329}
Submission and Validation
Upon submitting this flag, it was confirmed as correct.
Enjoy Reading This Article?
Here are some more articles you might like to read next: